TOP 5 THREAT RISK ASSESSMENT APPROACHES FOR CYBER SECURITY PROFESSIONALS
In this world full technical advancements, threat risk assessment mean different things to different people. Whether entrepreneurs, cyber security professionals, police, military personnel, psychologists, and counselors all use the same term threat risk assessment and conduct tasks that are all predictive in nature, but distinctive.
WHAT ARE THE COMMON THREAT RISK ASSESSMENT APPROACHES
In a conjugated term of threat risk assessment, there is also a difference between threat and risk, and here you can see how it is detangled. Let’s take a deeper dive into each threat and risk assessment approach.
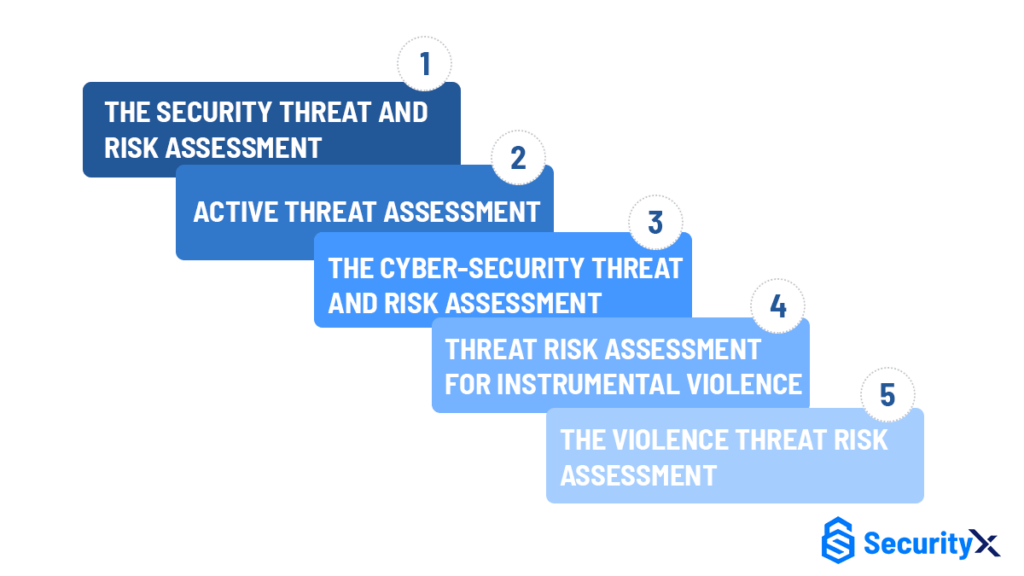
Common Threat Risk Assessment Approaches
-
THE SECURITY THREAT AND RISK ASSESSMENT
To people who work in the security or protection industry, threat assessment is the first step in a risk and vulnerability analysis. This threat assessment task involves assessing the various threats and security risks associated with a particular location. It covers a broad range of threats, ranging from natural threats, criminal threats, to terrorists and potential accidents. The security risk threat assessment is the precursor to a vulnerability assessment. This vulnerability assessment has two parts. First, it involves a determination of the loss that would be incurred if a given location was successfully attacked. Basically, how much will it cost if the facility stops providing service. Second, it also includes an assessment of the level of attractiveness of the target and the level of existing defenses against each different threat.
-
ACTIVE THREAT ASSESSMENT
For security professionals, threat risk assessment is also used to describe a process through which your operational personnel observe and identify potential, immediate, or imminent threats. Active threat assessment involves a focused observation of behaviors & actions. It is a threat assessment methodology by which an observer systematically observes their environment, identifies potentially suspicious individuals, and assesses the extent that person is a threat.
LET’S DIG DEEP INTO THE DEEP WEB SEARCH ENGINES
-
THE CYBER-SECURITY THREAT AND RISK ASSESSMENT
The same threat and risk assessment and analysis process can be applied to cyber-security. A cyber-security threat risk assessment can involve protecting information, networks, software, and hardware. The basic steps of a cyber-security risk assessment involve:
- Characterizing the type of system that is at risk
- Identifying threats to that system (unauthorized access, misuse of information, data leakage/exposure, loss of data, disruption of service)
- Determine inherent risks and impacts
- Analyze and identify threat prevention, mitigation, detection, and compensation controls. Assess the extent existing controls mitigate the threats.
- Determine the likelihood of a threat occurring based on current controls
- Calculate risk rating based on a combination of impact and likelihood.
As with the security threat risk assessment, it is then possible to implement or improve controls based on the higher risk threats to cyber-related infrastructure.
-
THREAT RISK ASSESSMENT FOR INSTRUMENTAL VIOLENCE
The vetted professionals in the industry describes another threat assessment approach that involves a broad spectrum of activities to identify and intervene with potentially violent individuals and prevent instrumental violence. It focuses on preventing a violent incident and to help potential offenders overcome the underlying sources of their anger, hopelessness, or despair.
This approach is focused on assessing the threat of a specific individual committing a specific attack. In your case, it could involve an employee who has made threats about against other staff members or has been involved in recent altercations at work.
-
THE VIOLENCE THREAT RISK ASSESSMENT
Violence threat risk assessments are generally legal and clinical in nature, estimating the likelihood of future violent behavior by an individual and the identification of risk factors and intervention strategies. This approach is somewhat different than the threat assessment for instrumental violence described above. This violence-risk approach focuses on assessing an individual’s predilection for violence generally, not related to a specific attack against a specific target. This threat assessment approach may not be something you or your personnel perform directly, often these assessments are conducted by experienced clinicians. These violence threat risk assessments can be used in release decisions for corrections and psychiatric facilities, civil commitment, criminal sentencing, or classification after admission into a correctional or treatment facility.
HOW WE EVOLVE WITH THE THREAT RISK ASSESSMENT PROCESS?
If you spare a moment to think about what threat risk assessment means to you or even what problem you are hoping that threat risk assessment will help you solve. Here are a few common threats that you need to give a look at:
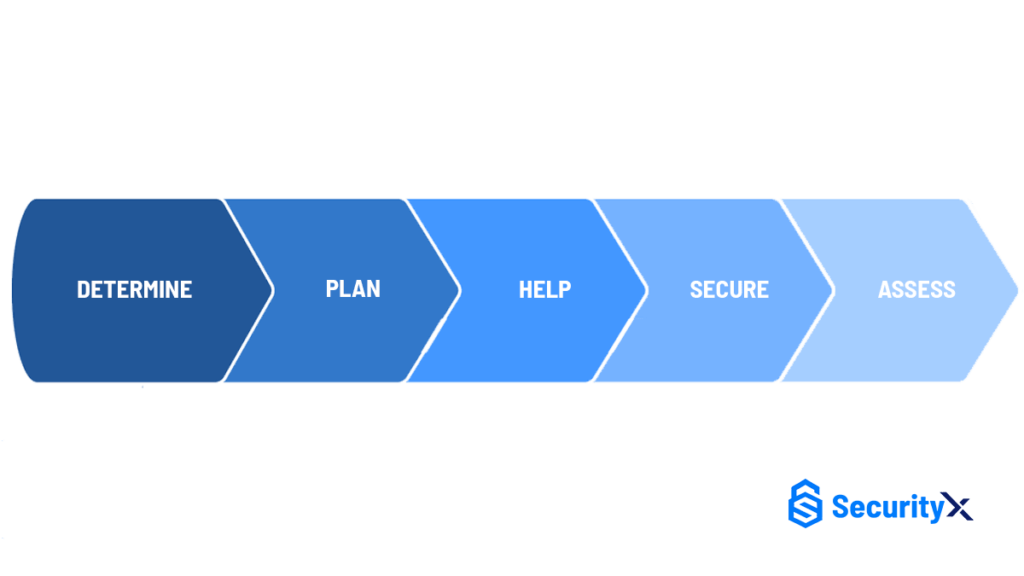
Threat Risk Assessment Process
DETERMINE
You can identify, assess, and intervene with a person who may commit targeted or instrumental violence with threat risk assessment.
TOP 10 EMERGING BENEFITS FOR CLOUD BASED MANAGED SERVICES
PLAN
Plan before you make a move and protect your data with optimum facilities and critical infrastructure against terrorist attacks, insider threats, natural disasters, and other threats.
HELP
Threat risk assessment help your security personnel identify and react to threatening individuals such as active shooters and cyber threats.
SECURE
Threat risk assessment security services protect your computer networks, systems, and servers from attacks by malicious actors.
HOW TO REMOVE TROVI SEARCH FROM THE WEB BROWSER?
ASSESS
Cyber security services allows you to assess the likelihood of a specific individual for violent behavior against your employees or clients.
IN CONCLUSION
Depending on your needs, any of these approaches to threat and security assessment may be relevant to you or your personnel. As a next step, take a deeper dive into more updates and similar threat risk assessment blogs that you can find at Securityx.

0 Comments