WHAT IS INFORMATION RISK MANAGEMENT? UNDERSTAND IT BETTER!
Do you wonder what information risk management is? Well, the information risk management is defined as the policies, procedures, and technology an organization adopts in order to reduce the threats, vulnerabilities, and consequences that could arise if data is not protected. Here, you’ll see how the classic equation for risk can help you prioritize your information risk management strategy and recommend best practices for doing so.
WHY YOU NEED TO UNDERSTAND THE IT RISK EQUATION?
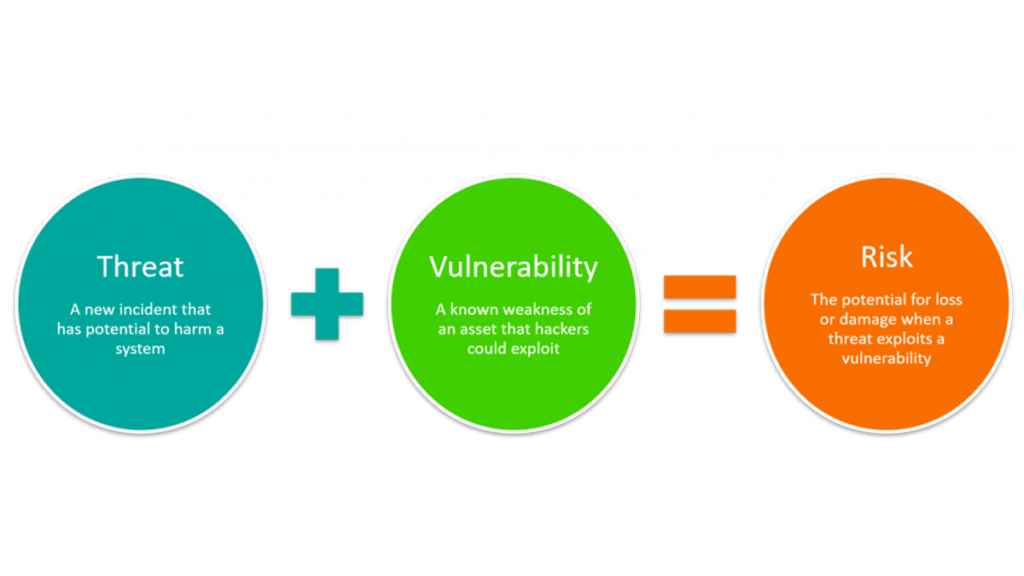
WHY YOU NEED TO UNDERSTAND THE IT RISK EQUATION
As mentioned in our working definition, IT risk management examines this classic equation for risk which includes threat, vulnerability and consequences.
WHAT IS A THREAT?
WHAT IS A THREAT
Threat is inherent in information risk management, and most organizations assume that their vendors present at least some level of threat.
WHAT IS VULNERABILITY?
WHAT IS VULNERABILITY
Vulnerability comprises the gaps in a protection program. Let’s say you have a really sensitive document and you put it in a safe, in a locked building, protected by guards; you likely feel confident that the document isn’t vulnerable to many threats. Now, if that same document was online in an open network where your organization stores all of its data, it’s easy to understand how the safety of the document is compromised. The moral of this story is to understand not only what vulnerabilities are in your protection program, but also how those vulnerabilities can be exploited. Once you parse through this information, you’ll gain a clearer idea of how to address your overall risk.
WHAT ARE THE 4 MAIN TYPES OF VULNERABILITY?
WHAT ARE THE CONSEQUENCES?

WHAT ARE THE CONSEQUENCES
Consequence represents the harm caused to an organization by a cyberattack. An important element to consider here is the value of the information you’re trying to protect something which can vary tremendously. For example, intellectual property data or pricing information may be of value to your organization. But data, such as personally identifiable information (PII), can also hold value because of the legal requirements to protect it.
HOW TO CONDUCT INFORMATION RISK MANAGEMENT
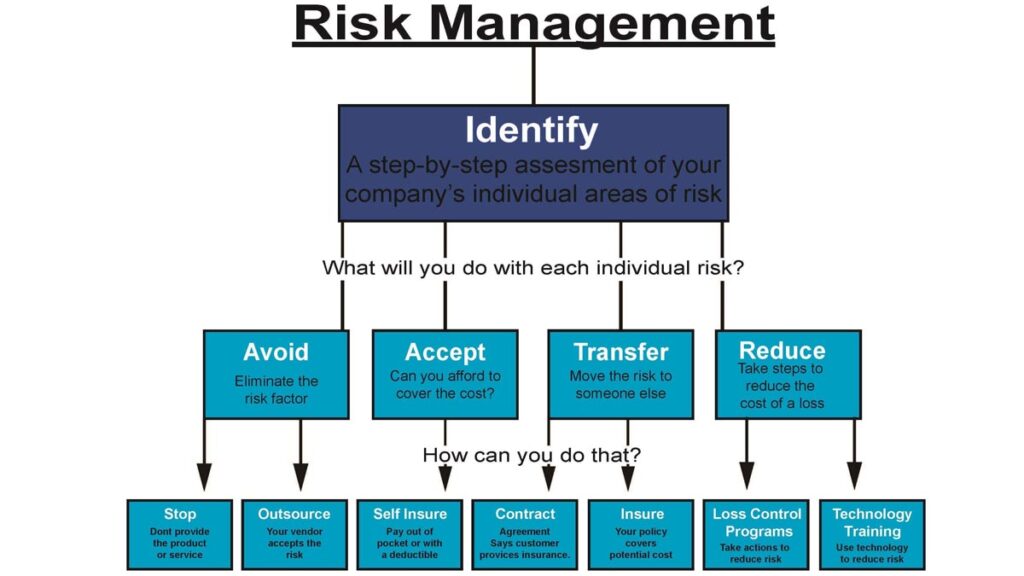
HOW TO CONDUCT INFORMATION RISK MANAGEMENT
Knowing what IT risk management is and what it entails, as outlined by the risk equation, is the first step to managing that risk. From here you can take the next step of establishing a clear strategy for information security and risk management. It’s important to note that this strategy is typically set by the leadership in an organization. Data is the lifeblood of so many companies so the task of managing information risk isn’t and shouldn’t be taken lightly.
Once senior executives set an IT risk management (IRM) strategy, it’s contingent on the rest of the organization. From HR to legal, marketing to finance you need to set policy into action. The policies are written and distributed throughout the organization, so all employees understand the severity of any risk management infractions.
The information risk management strategy also serves as a guideline for IT security teams to implement the technical controls (firewalls, intrusion detection, multi-factor authentication, etc.) they need to help avoid or lessen the impact of a catastrophic data breach.
To mitigate third, fourth, and even nth party risk, vendor Risk Management teams must work with vendors, suppliers, and other parties critical to business operations to make sure that they have reasonable information security policies in place. These combined efforts help ensure that a company doesn’t suffer from the harm they’re trying to stay away from.
WAYS TO FREE UP SPACE ON YOUR DESKTOP
EVERYONE IS RESPONSIBLE

EVERYONE IS RESPONSIBLE
Information risk management is not something that lies with IT or security teams; it’s an imperative that the whole organization must own. In other words, this is not something to swiftly pass over or delegate to a low-level intern. IT risk management requires senior leadership involvement. There are simply too many intentional and unintentional threats to an organization’s data, and if these issues are ignored, the consequences could be severe. Financial, legal, and reputational harm could befall those that do not take this advice into consideration so for an improved information risk management strategy, you need to make sure that you even stay prepared for the worst.
WHY YOU NEED INFORMATION RISK MANAGEMENT?

WHY YOU NEED INFORMATION RISK MANAGEMENT
Regardless of your risk acceptance, information risk management programs and special campaigns are an increasingly important part of enterprise risk management. Companies are increasingly hiring Chief Information Security Officers (CISO) and turning to cybersecurity software to ensure good decision making and strong security measures for their information risk management systems. And these tactics are eventually helping them without causing any hassle or delays.
TOP 5 THREAT RISK ASSESSMENT APPROACHES FOR CYBER SECURITY PROFESSIONALS
WHY CYBER RISK MANAGEMENT MUST BE A PART OF INFORMATION RISK MANAGEMENT?
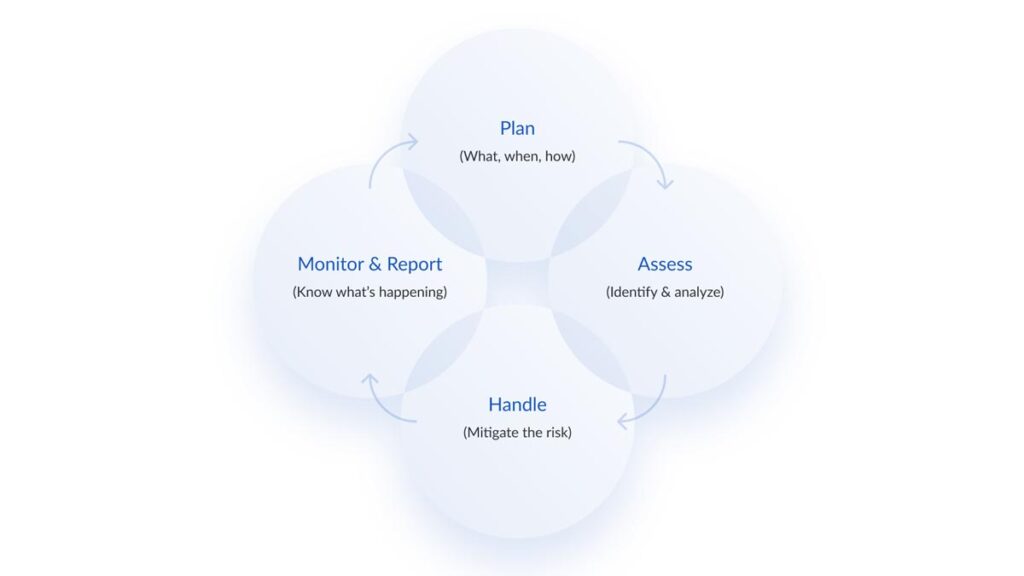
WHY CYBER RISK MANAGEMENT MUST BE A PART OF INFORMATION RISK MANAGEMENT
Every organization should have comprehensive information risk management in place that addresses four categories:
- Strategy: High-level goals aligning and supporting the organization’s mission
- Operations: Effective and efficient use of resources
- Financial reporting: Reliability of operational and financial reporting
- Compliance: Compliance with applicable laws and regulations
Cyber risk transverses all four categorizes and must be managed in the framework of information security risk management, regardless of your organization’s risk appetite and risk sensitivity. And for more updates, simply contact Securityx anytime, anywhere!

0 Comments